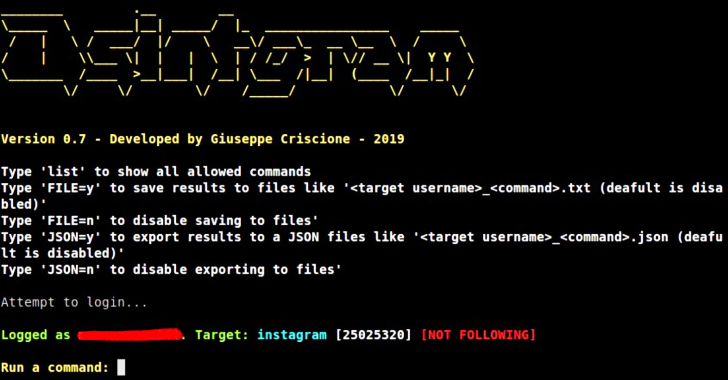
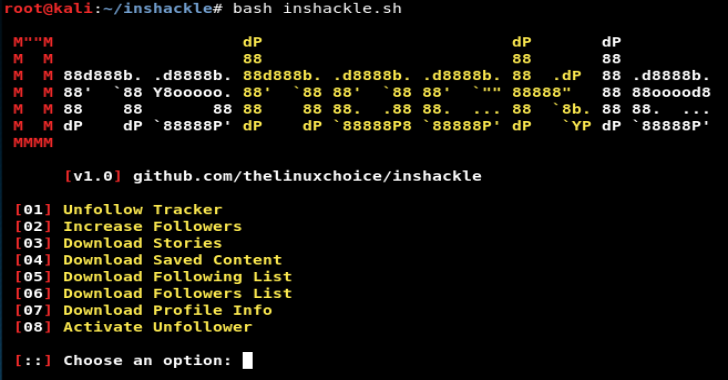
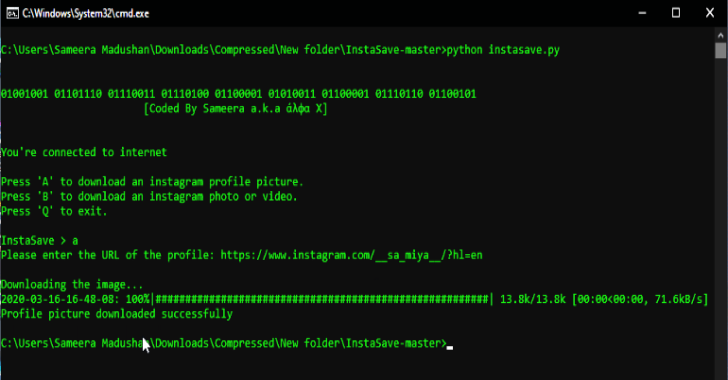
Terra is a OSINT Tool On Twitter And Instagram. Installation Clone the github repo $ git clone https://github.com/xadhrit/terra.git Change Directory $ cd terra Requirements For requirements run following commands: $ python3 -m pip install -r requirements.txt Note For Twitter Credentials : You need credentials which are listed in twitter.yml file in creds folder for using terra. You …
Continue reading “Terra : OSINT Tool On Twitter And Instagram”