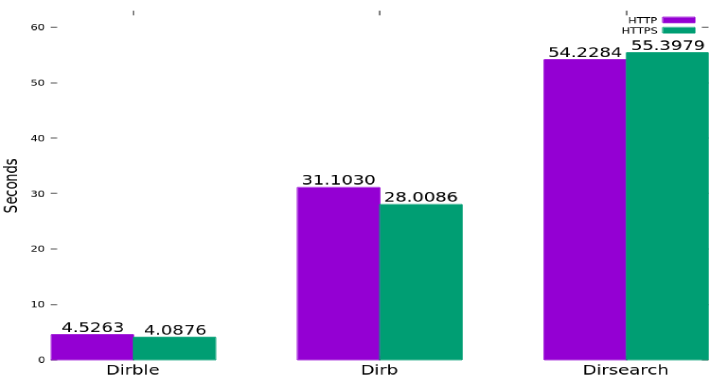
Do you need to filter Nessus scan results and zero in on exploitable vulnerabilities? When you’re on a penetration test or vulnerability assessment and you have to review Nessus scan results, you can filter using Nessus or you can export a Nessus .nessus file for distrubution or offline parsing. Nessusploitable parses .nessus files for exploitable …
Continue reading “Nessusploitable – Targeting Exploitable Nessus Vulnerabilities”
%20(1).webp)
.png)