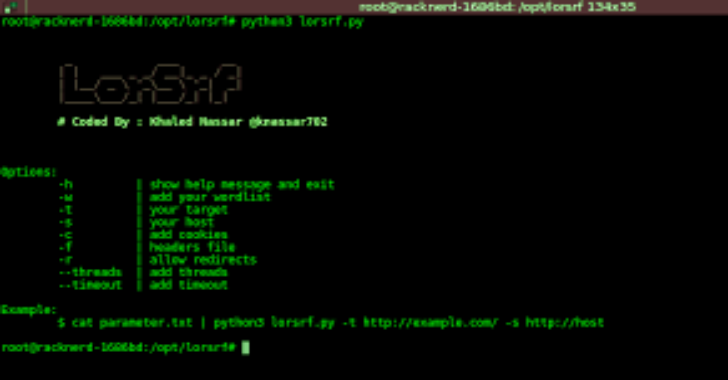
Lorsrf has been added to scant3r with useful additions (multi http method , multi content-type (json , query , xml , speed , large worlist and more)). Bruteforcing on Hidden parameters to find SSRF vulnerability using GET and POST Methods Install download it ➜ git clone https://github.com/knassar702/lorsrf➜ cd lorsrf➜ sudo pip3 install requests flask install ngrok tool Steps Ngrok run your ngrok ./ngrok …
Tag Archives: bruteforce
Shreder : A Powerful Multi-Threaded SSH Protocol Password Bruteforce Tool
Shreder is a powerful multi-threaded SSH protocol password brute-force tool. Features Very fast password guessing, just one password in 0.1 second. Optimized for big password lists, Shreder tries 1000 passwords in 1 minute and 40 seconds. Simple CLI and API usage. Installation pip3 install git+https://github.com/EntySec/Shreder Basic Usage To use Shreder just type shreder in your terminal. usage: shreder [-h] [-p PORT] [-u USERNAME] …
Continue reading “Shreder : A Powerful Multi-Threaded SSH Protocol Password Bruteforce Tool”
URLBuster : Powerful Mutable Web Directory Fuzzer To Bruteforce
URLBuster is a powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot of mutation options. Installation pip install urlbuster Features Proxy support Cookie support Basic Auth Digest Auth Retries (for slow servers) Persistent and non-persistent HTTP connection Request methods: GET, POST, PUT, DELETE, …
Continue reading “URLBuster : Powerful Mutable Web Directory Fuzzer To Bruteforce”
RMIScout : Bruteforce Attacks Against Exposed Java RMI Interfaces
RMIScout performs wordlist and bruteforce attacks against exposed Java RMI interfaces to safely guess method signatures without invocation. On misconfigured servers, any known RMI signature using non-primitive types (e.g., java.lang.String), can be exploited by replacing the object with a serialized payload. This is a fairly common misconfiguration (e.g., VMWare vSphere Data Protection + vRealize Operations …
Continue reading “RMIScout : Bruteforce Attacks Against Exposed Java RMI Interfaces”
ShuffleDNS : Wrapper Around Massdns Written In Go To Enumerate Valid Subdomains Using Active Bruteforce
ShuffleDNS is a wrapper around massdns written in go that allows you to enumerate valid subdomains using active bruteforce as well as resolve subdomains with wildcard handling and easy input-output support. Features Simple and modular code base making it easy to contribute. Fast And Simple active subdomain scanning. Handles wildcard subdomains in a smart manner. …
DeepSearch – Advanced Web Dir Scanner For Bruteforce
DeepSearch is a simple command line tool for bruteforce directories and files in websites. you can also use Dark web browser to surf anonymously. DeepSearch Installation $ git clone https://github.com/m4ll0k/DeepSearch.git deepsearch $ cd deepsearch $ pip3 install requests $ python3 deepsearch.py Also ReadInvisi-Shell : Hide Your Powershell Script In Plain Sight(Bypass all Powershell security features) …
Continue reading “DeepSearch – Advanced Web Dir Scanner For Bruteforce”
BruteX – Automatically Brute Force All Services Running On A Target
BruteX is a tool to automatically brute force all services running on a target. As you all know a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found It include the …
Continue reading “BruteX – Automatically Brute Force All Services Running On A Target”
Hatch – Brute Force Tool That Is Used To Brute Force Most Websites
Hatch is a brute force tool that is used to brute force most websites. In order to use the this tool you need the following requirements. pip2 install seleniumpip2 install requests Note : chrome driver and chrome are also required! link to chrome driver: http://chromedriver.chromium.org/downloads copy it to bin. Also Read:ImaginaryC2:Python Tool Help In Network Behavioral Analysis …
Continue reading “Hatch – Brute Force Tool That Is Used To Brute Force Most Websites”
Dirhunt – Find Web Directories Without Bruteforce
Dirhunt is a web crawler optimize for search and analyze directories. This tool can find interesting things if the server has the “index of” mode enabled. Dirhunt is also useful if the directory listing is not enabled. It detects directories with false 404 errors, directories where an empty index file has been created to hide …
Continue reading “Dirhunt – Find Web Directories Without Bruteforce”
SQLMAP – Enumeration of Databases & Users from Vulnerable Web Forms
Sqlmap is a database assessment tool which pentesters & security researchers can use to enumerate databases of various types. Sqlmap automates a normal & advanced sql injection techniques and performs them on a regular form. Refer to the article on Introduction to SQLMAP for getting started. The following lab sessions are a continuation of the previous …
Continue reading “SQLMAP – Enumeration of Databases & Users from Vulnerable Web Forms”